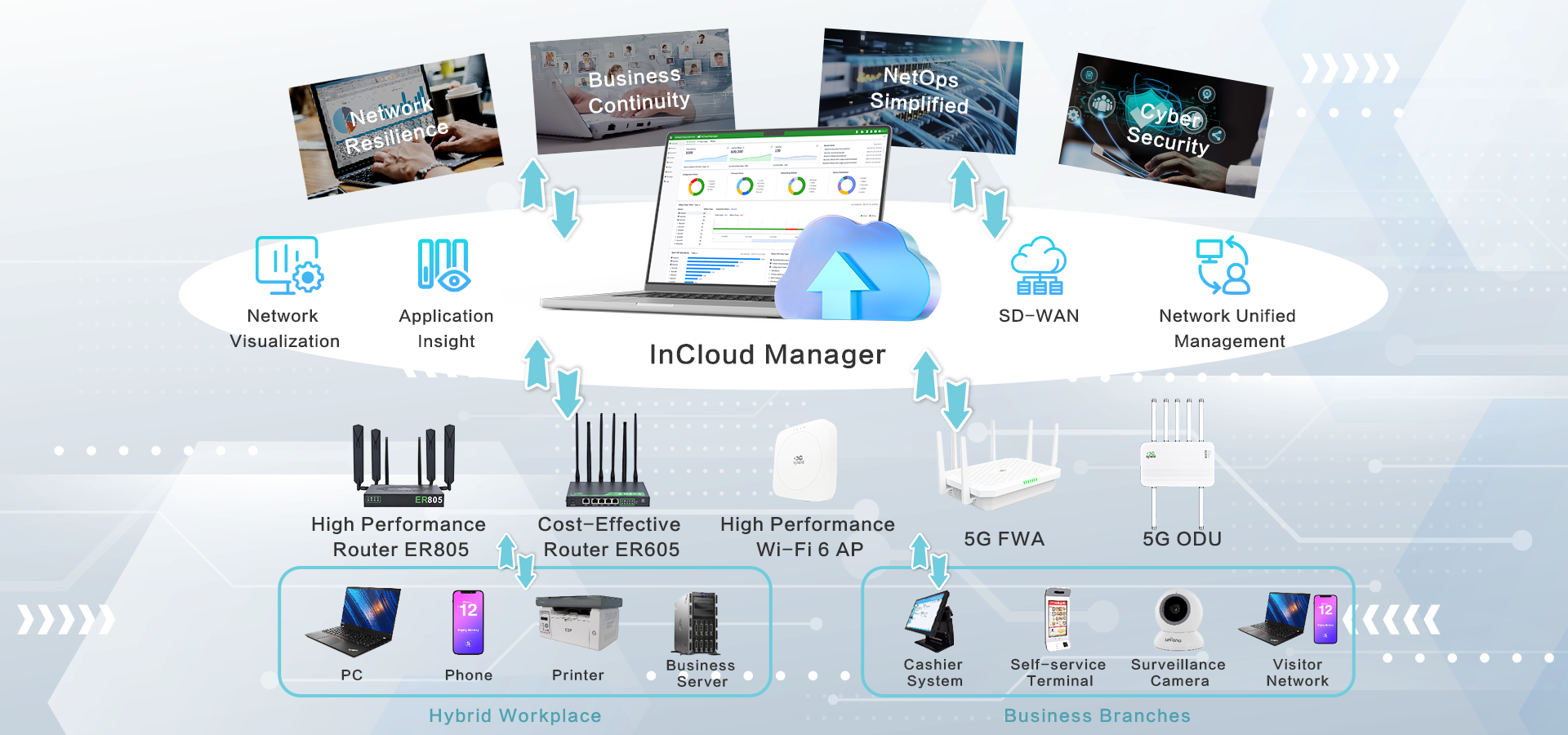
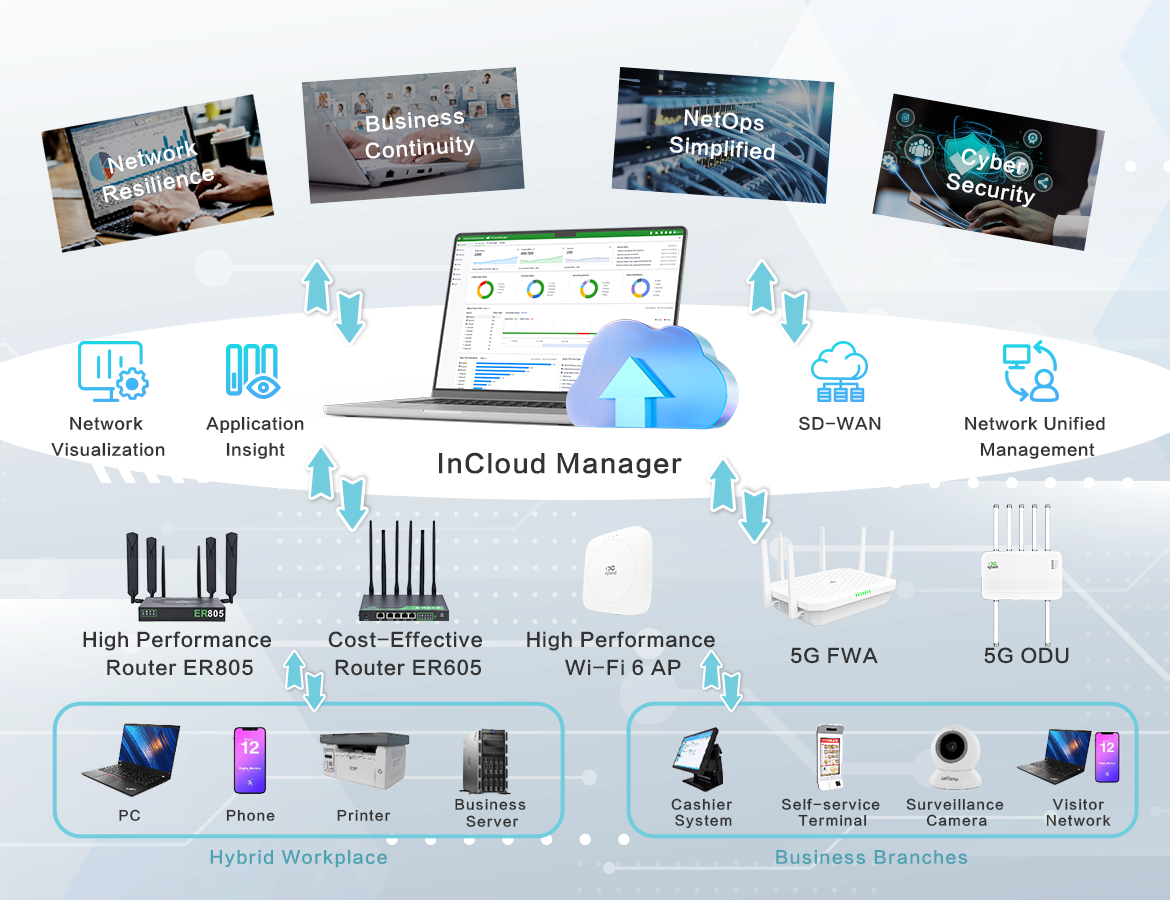
InHand Cloud-Managed Networking Solution
In this digital age, InHand Networks offers a cutting-edge cloud-managed networking solution that empowers enterprises. Our solution encompasses cloud-managed edge routers, Wi-Fi access points, switches, 5G FWA/ODU cellular routers, and the InCloud Manager SaaS. By integrating top-tier IT management, IoT, 5G, and other technologies, we provide fast, secure, and user-friendly network solutions globally, enabling businesses to unlock boundless growth opportunities.
Highly available networks
- Benefit from integrated wired, cellular, and Wi-Fi connectivity, enabling redundancy and backup systems to minimize single points of failure.
- Enjoy automatic failover and load balancing to reroute network traffic for seamless service continuity and minimal downtime.
- Guarantee the connectivity with off-site backups and out-of-band management to quickly recover network services during major disruption.
Redefine the way IT is managed
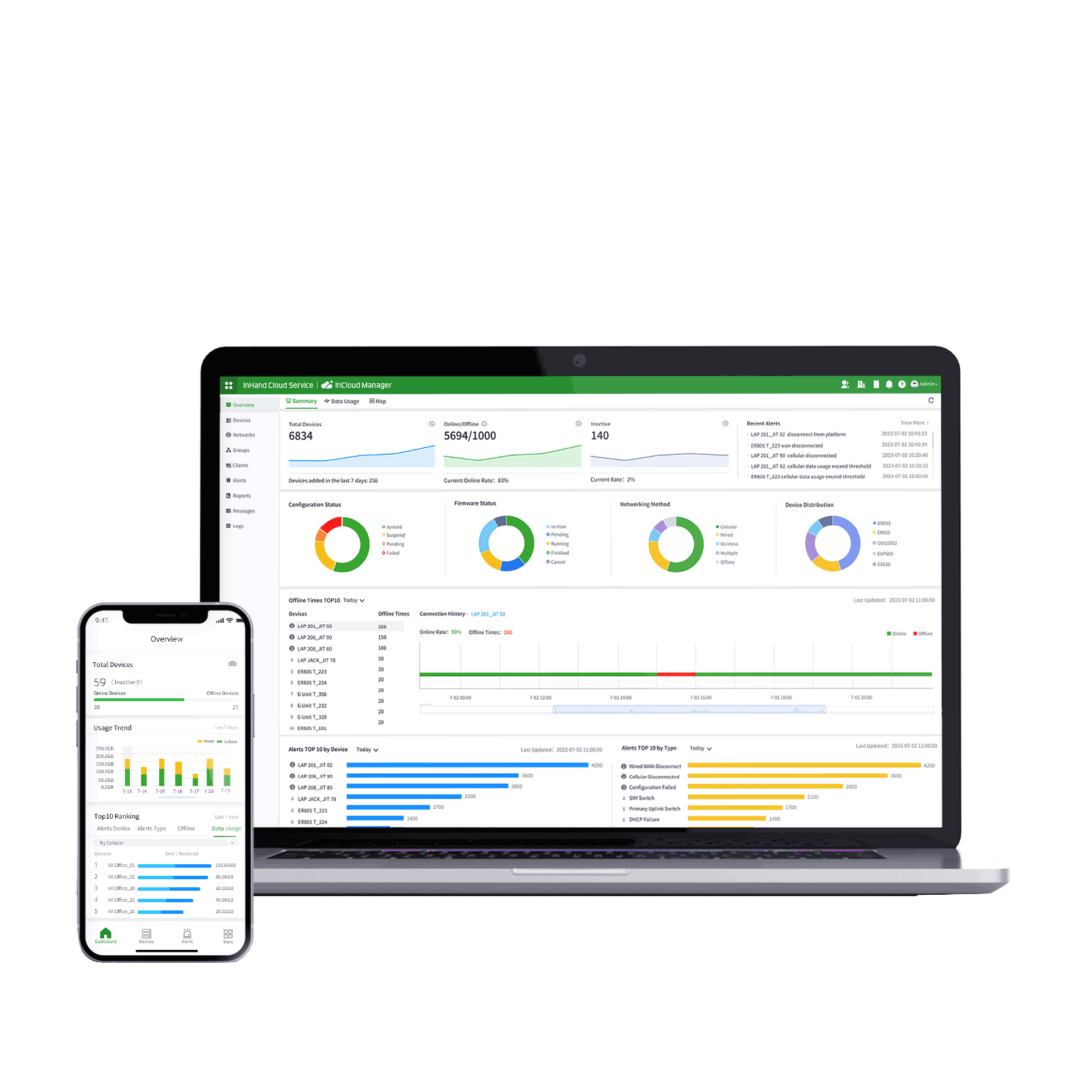
We provide a centralized platform to streamline your network management.
- Deploy thousands of networks quickly with cloud configuration and automated orchestration to easily scale your network up.
- Monitor WAN, access, and IoT technologies with end-to-end visibility all in InCloud Manager, empowering flexibility for teams.
- Visualize network performance, traffic patterns, and device health for valuable insights to optimize the network.
Improve network agility and continuity
- Gain agile responses to specific needs for each site with our plug-and-play devices and clouds to maintain productivity.
- Multi-dimensional data reports help IT teams quickly implement updates, patches, and configuration adjustments to ensure efficient network operation.
- Accurate identification of network applications and fine-grained traffic control ensure adequate bandwidth for critical business.


Enhance cyber security
Our solution enables agile response to threats across networks, applications, endpoints, and clouds.
- Gain insights into encrypted traffic with multiple security policies like firewalls, threat identification, and intrusion detection, proactively preventing unpredictable attacks.
- Enhance protection through data encryption transmission, multi-factor identity authentication, and role-based access control.
- Rest assured of our data privacy, as no business-related data is uploaded to the cloud.